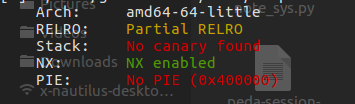
0x01 漏洞点
1 | int __cdecl main(int argc, const char **argv, const char **envp) |
0x02 攻击
1 | 由于echo拷贝时,会被\x00截断,所以不能连续覆盖多个地址来rop, |
0x03 exp
1 | from pwn import * |

1 | int __cdecl main(int argc, const char **argv, const char **envp) |
1 | 由于echo拷贝时,会被\x00截断,所以不能连续覆盖多个地址来rop, |
1 | from pwn import * |